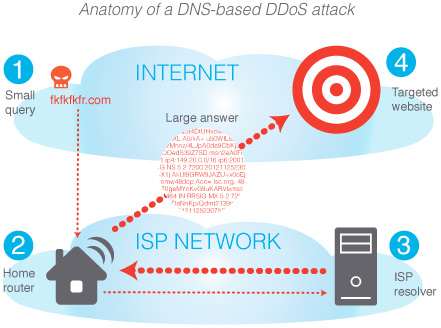
Researchers from nominum identified a massive set of of DNS-based DDoS amplification attacks have significantly increased in the recent months, targeting vulnerable home routers globally.
( A DNS amplification attack is a reflection-based distributed denial of service (DDos) attack )
Home routers are the easiest vector of attack because most users are unaware of the security implications. The router firmware are never updated which leaves it in the open to all kinds of attacks. Hackers use this as their target and find ways to infiltrate the vulnerable routers.
Nominum researchers observed that :
- Tens of millions of home routers expose provider networks to DNS-based DDoS
- Stealthy, low-skill attack evades existing defenses and Best Practices
- Attackers constantly register new “purpose built” domains only for amplification
- Substantial network impact: DNS servers, access networks, peering and transit
- Subscriber-perceptible attacks spike support calls, reduce satisfaction, stress ops teams
Traffic from amplification amounts to trillions of bytes a day disrupts ISP’s, websites and individuals. Impacts of such attacks on on ISPs are fourfold:
- Network impact generated by malicious traffic saturating available bandwidth
- Cost impact generated by a spike in support calls caused by intermittent service disruption
- Revenue impact as poor internet experience leads to increased churn or retention expenses
- Reputation impact as unwanted traffic is directed toward peers