What was first considered a ransomware attack turned into a much more complicated situation as researchers at the Slovakian security software firm ESET found a backdoor written into some software updates the Ukrainian M.E.Doc, the main source of infection breakout unleashed last week in Ukraine.
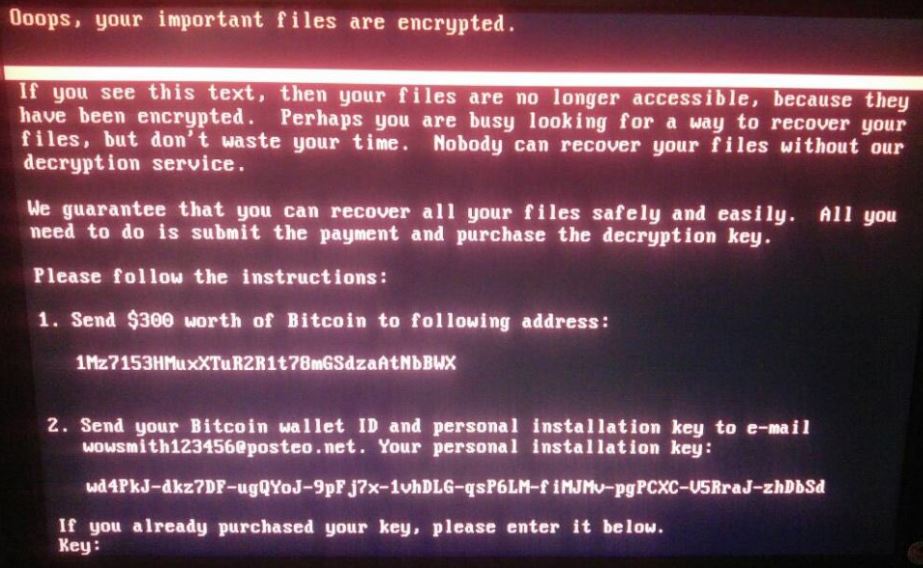 According to a post by Security Week, ESET researchers had performed an exhaustive analysis of the infected software and found out that the malware identified as NotPetya was intended to remove data not withhold it encrypted for money. Reuters had reported earlier, but could not confirm, an announcement allegedly by the people behind the attack demanding 256,000$ in bitcoins in return for decryption of all infected devices.
According to a post by Security Week, ESET researchers had performed an exhaustive analysis of the infected software and found out that the malware identified as NotPetya was intended to remove data not withhold it encrypted for money. Reuters had reported earlier, but could not confirm, an announcement allegedly by the people behind the attack demanding 256,000$ in bitcoins in return for decryption of all infected devices.
However, researchers linked the attack with TeleBots, a persistent threat group previously known as BlackEnergy and Sandworm. The cybercriminals in questions had made several attempts to compromise Ukrainian establishments before. Their choice of M.E.Doc is rather interesting. The tax accounting software is used by 80 percent of the Ukranian companies and is installed on around 1 million computers across the country.
Researchers confirmed that had the attackers not had access to the source code, the backdoor installation in the software would not have been possible. They estimated that the attackers had the source code since the beginning of the year. Infectious updates were distributed at least three times: as early as April 14th as a test, on May 15th to drop the XData ransomware which comprised the smokescreen attack to distract attention and on June 22nd to drop NotPetya.
These updates occurred without alarming the M.E.Docs developers as several other clean updates were released during that time.
The 5 megabytes backdoor written in .NET framework was injected in one of the application modules and then pushed as an update. The methods of the backdoor class which is called MeCom are invoked by the request for updates called periodically by the legitimate code to check for updates. Therefore, attackers were able to send the harvested information in cookies files without generating alarmingly excessive network traffic.
The backdoor also features code that gives cybercriminals the chance to control infected machines through a binary blob the analysis of which revealed it to be “an XML file that could contain several commands at once.”
The commands include but are not limited to: RunCmd, DumpData, MinInfo, GetFile, Payload and AutoPayload.
According to ESET notes, this makes the backdoor a “fully-featured cyberespionage and cybersabotage platform at the same time” since using this commands will allow attackers to run shell command, gather system and user information such as proxies, emails and passwords, collects files and execute payloads.
The malicious backdoor allows the attackers to know exactly which organisation were infected using EDRPOU a unique legal entity identifier all companies in Ukraine have and thus target specific companies with customised strategies.
The backdoor kept the harvested data waiting to be sent in the Windows registry under the HKEY_CURRENT_USER\SOFTWARE\WC key. According to ESET, this will allow investigators to distinguish compromised machines. Although malware fingerprints were found on network-connected devices that didn’t even have the infected software installed, which means that the size of the attack is yet unknown and other backdoors are probably still out there waiting for a signal.
Due to security reasons, M.E.Doc servers were seized by the police and experts could not perform a forensic analysis. However, ESET researchers are sure the servers were compromised.
As the servers remain offline, further updates to resolve the backdoor are still not possible and many unanswered questions will keep everyone working on the matter awake at night until they know for sure: for how long the backdoor had been activated and whether or not it was used to distribute other malware.
What we might view as worthy discoveries, the Ukrainian police views as a national security threat as major companies across Ukraine were compromised. The M.E.Doc servers were seized by the police pending investigations, the Russian government was initially accused of the attack and now Ukraine’s security service is teaming with NATO to better deal with future cyber threats.
The preparation and patience the attackers behind the NotPetya demonstrated are both admirable and disturbing; many researchers agree that we have not yet seen the end of this well-planned attack. Hopefully, any other backdoors will be detected and contained before the attackers’ next move.
