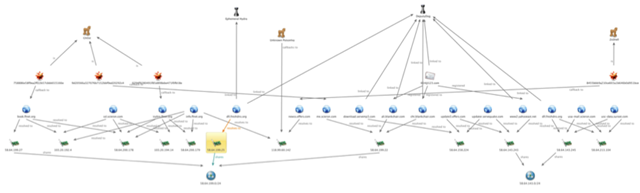
 Recently a zero day vulnerability in Internet Explorer was discovered(CVE-2014-0322)). Researchers from Fireeye has identified that hackers are using this vulnerability in targeting US military personals. Furthermore they also suspect that this may be a very strategic campaign (Operation Snowman) during the President’s day weekend.
Recently a zero day vulnerability in Internet Explorer was discovered(CVE-2014-0322)). Researchers from Fireeye has identified that hackers are using this vulnerability in targeting US military personals. Furthermore they also suspect that this may be a very strategic campaign (Operation Snowman) during the President’s day weekend.
Fireye further says :
“The attacker uses the Microsoft.XMLDOM ActiveX control to load a one-line XML string containing a file path to the EMET DLL. Then the exploit code parses the error resulting from the XML load order to determine whether the load failed because the EMET DLL is not present. The exploit proceeds only if this check determines that the EMET DLL is not present.
Because the vulnerability allows attackers to modify memory to an arbitrary address, the attacker can use it to bypass ASLR. For example, the attacker corrupts a Flash Vector object and then accesses the corrupted object from within Flash to access memory. We have discussed this technique and other ASLR bypass approaches in our blog. One minor difference between the previous approaches and this attack is the heap spray address, which was changed to 0x1a1b2000 in this exploit.
Once the attacker’s code has full memory access through the corrupted Flash Vector object, the code searches through loaded libraries gadgets by machine code. The attacker then overwrites the vftable pointer of aflash.Media.Sound() object in memory to point to the pivot and begin ROP. After successful exploitation, the code repairs the corrupted Flash Vector and flash.Media.Sound to continue execution.”
