With the rise of Bitcoin media publicity, fraudsters are finding new ways to get their share of piece of it.
Recently mass targeted scam/phishing email is being delivered to users email addresses whose might have been scraped from popular Bitcoin sites or stolen in security breaches: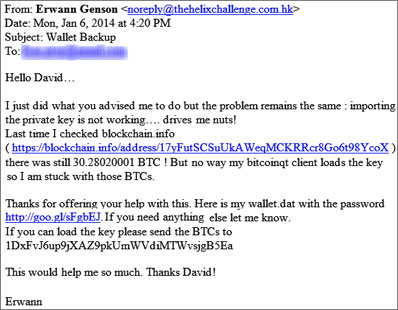
As per Logrhythm security researchers, email comes from Amazon’s Simple Email Service and not from actual email address.
When a user clicks on the link on the email, the user will be sent to the malicious site downloading Backup.zip.
Several files are zipped: bitcoinqt.png, password.txt,password.txt.lnk, & wallet.dat, but only the last two are visible unless “Show hidden files” The initially visible files prepare the ground for the attack, and the Password.txt file is actually a packed executable.
“Running this file launches a blank command prompt window, followed by a program masquerading as notepad, then the real notepad application, which displays the ‘password’ to the wallet.datfile,” the researchers explain.
“In reality, this program launches two files, one notepad.exe to display the fake password, and another file Password.txt which appears to actually be a backdoor’d version of ‘EditPlus’. This file continues to run silently and remains open even after notepad is closed.”
“Malware waits for the victims to open their BitCoin wallet using the BitcoinQT software, and when they do, they are showed a previously prepared screenshot of a digital wallet containing some 30 Bitcoin (the aforementioned bitcoinqt.png file).
The malware contacts the attackers’ network, and begins to empty their own wallets in the background. ” as per net-sec
Within less than 24 hours of campaign over 1,600 users clicked on the malicious link. The number of compromised users is unknown.
