A new version of the Zeus trojan, all time favorite of criminals for financial fraud has been used in attacks on over 30,000 electronic banking customers in Europe, infecting both their personal computers and smartphones. The sophisticated attack is designed to circumvent banks’ use of two-factor authentication for transactions by intercepting messages sent by the bank to victims’ mobile phones.

Pic : netsecurity/Checkpoint
The malware and botnet system, dubbed “Eurograbber” by security researchers from Check Point Software and Versafe, was first detected in Italy earlier this year. It has since spread throughout Europe. Eurograbber is responsible for more than $47 million in fraudulent transfers from victims’ bank accounts, stealing amounts from individual victims that range from 500 Euros (about $650) to 25,000 Euros (about $32,000), according to a report published Wednesday (PDF).
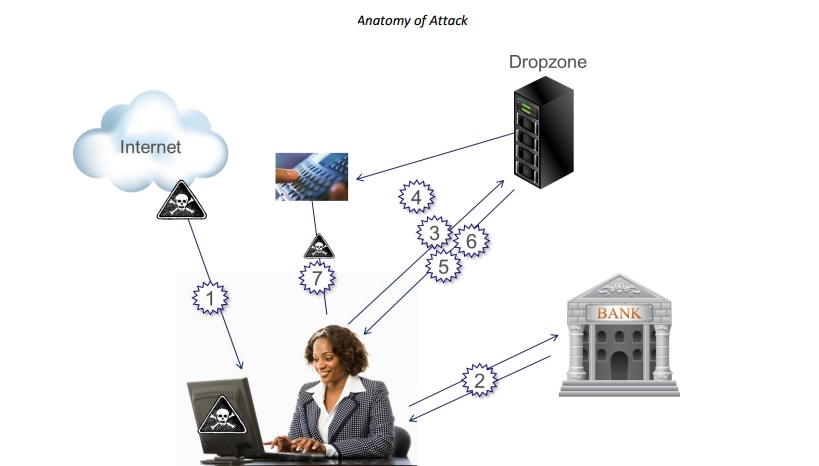
Netsec complied this into 10 stages, starting with an initial infection by a modified version of Zeus:
- Users’ PCs become infected by a modified Zeus trojan by accidentally visiting an infected web page, or following a link from a phishing email. This opened the door for the attack.
- Users visit their bank’s webpage and log in to their account to make a transaction.
- The modified Zeus trojan injects malicious code into the bank webpage, including a request for users to enter their mobile information, including its number and operating system.
- This information is sent over the Internet to the attacker’s “drop zone” system where it is stored.
- The attacker’s server sends an SMS message to the user’s mobile device that includes a link to the mobile device-targeting trojan, a version of Zitmo (Zeus in the mobile).
- User are directed to click on a link in the SMS to ‘upgrade the security of the online banking system’. This installs the mobile Trojan on the mobile device and completes the system.
- Now, every time the user logs into their bank account, the Trojan initiates an automatic transaction to transfer money out of the victim’s account using their real credentials.
- To complete the transaction, an SMS message containing the TAN is sent to the victim’s mobile device, and the mobile Trojan delivers the TAN to the attacker’s server.
- The customized Zeus Trojan Javascript running on the victim’s computer receives the TAN.
- The Eurograbber attack is complete and the attackers transfer money out of a victim’s account.
Pic : netsecurity/Checkpoint
The future of cyber attacks are becoming very sophisticated and the whole internet landscape has changed with increased security over time.
Complete paper is available on checkpointwebsite : here